
Linking an SSH key to Github is one of the key steps when securing your account. It allows you to harness the power of public-key cryptography to protect your Git repositories. This article will show you what SSH keys are and how you can use them to harden your Github account.
Note: new to Git? Learn from our getting started guide now.
What Are SSH Keys?
In gist, SSH keys are public keys that you store on a remote server. These act as an authentication proxy that allows you to connect and interact with machines without providing a username and password.
The way it works is that whenever you connect to a machine through SSH, your local computer sends a message signed by your private SSH key. The remote machine, then, uses your public SSH key to verify the message’s authenticity and log you in.
Github uses the same approach to verify your identity inside its servers. The website uses your public key whenever you upload and modify your repository. This ensures that you do not expose your Github credentials when pushing commits.
Good to know: Learn more about Public-Key Cryptography and how it can secure your online identity by installing GNU Kleopatra in Linux.
Generating SSH Keys For Github
To start, open a new terminal session using your distro’s application launcher.
Ensure that you have installed OpenSSH in your machine and the SSH agent daemon is currently running:
sudo apt install ssh eval `ssh-agent -s`
Run the following command to start the SSH key generation wizard:
ssh-keygen -t ed25519 -C "ramces@email.invalid"
The wizard will then ask you if you want to use a custom SSH keyfile name for your key. Press Enter to accept the default name and location.
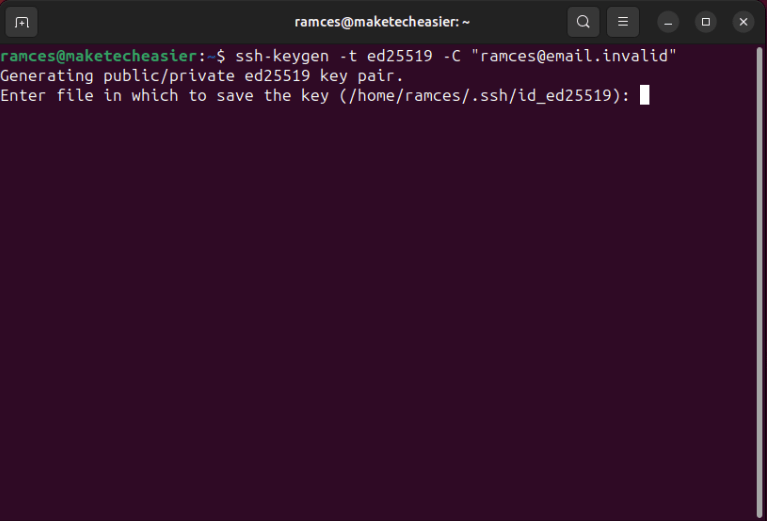
Type a password for your new SSH key. This will serve as your local machine’s passphrase whenever it connects to your Github account.
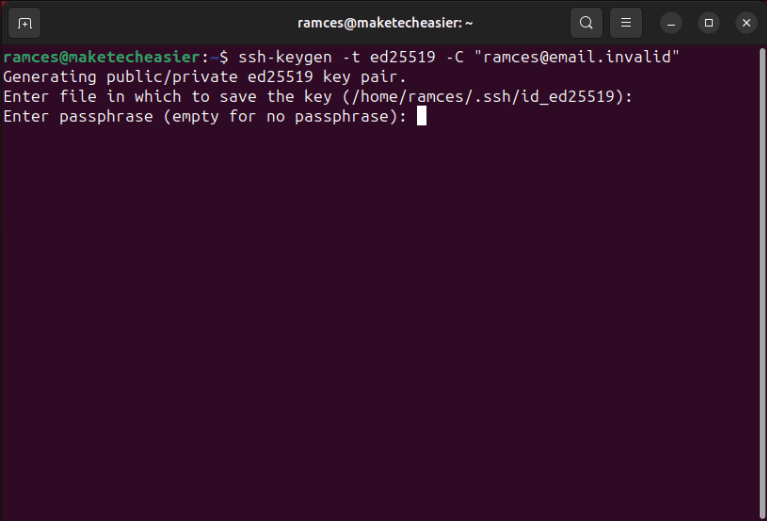
Note: You can also leave the password prompt blank if you want to create a password-less SSH key.
Add your newly generated SSH key to your currently running SSH agent:
ssh-add ~/.ssh/id_ed25519
Good to know: if you are new to Github, find out some of the best apps you should add to your Github repository.
Adding SSH Keys to Github
With your new SSH key up and running, you can now link your local machine to your Github account. To start, run the following command to print your SSH public key:
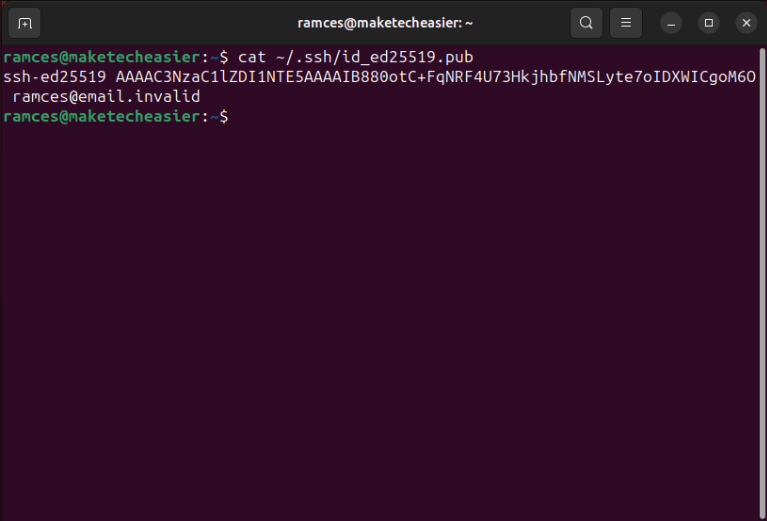
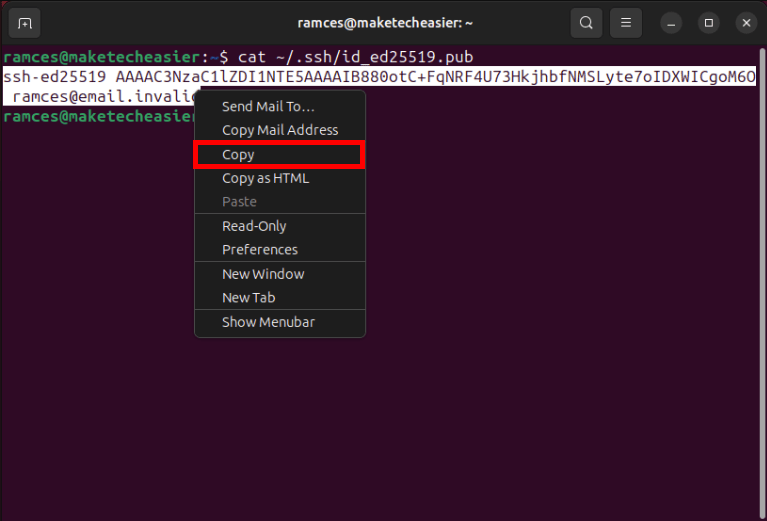
cat ~/.ssh/id_ed25519.pub
Highlight your SSH public key, press Right Click then select “Copy.”
Open a new browser session, then navigate to your Github homepage.
Click your profile icon on the upper right corner of the page.
Click “Settings” from the dropdown list.
Select “SSH and GPG Keys” along the left sidebar of the settings page.
Click the “New SSH Key” button beside the “SSH Keys” header.
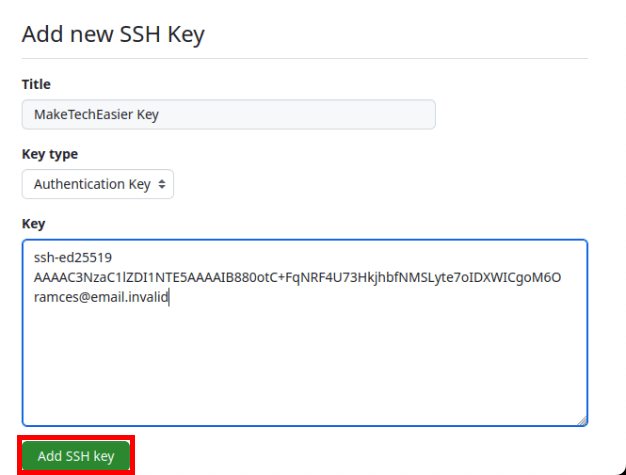
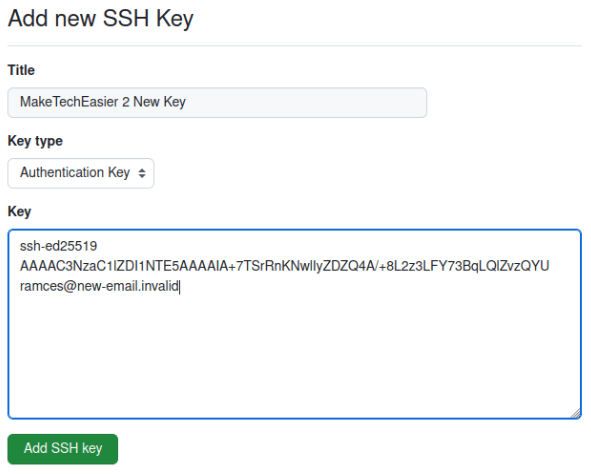
Select the “Title” textbox, then provide a name for your key.
Click the “Key” textbox, then press Ctrl + V to paste your SSH key.
Click “Add SSH Key” to commit your new settings.
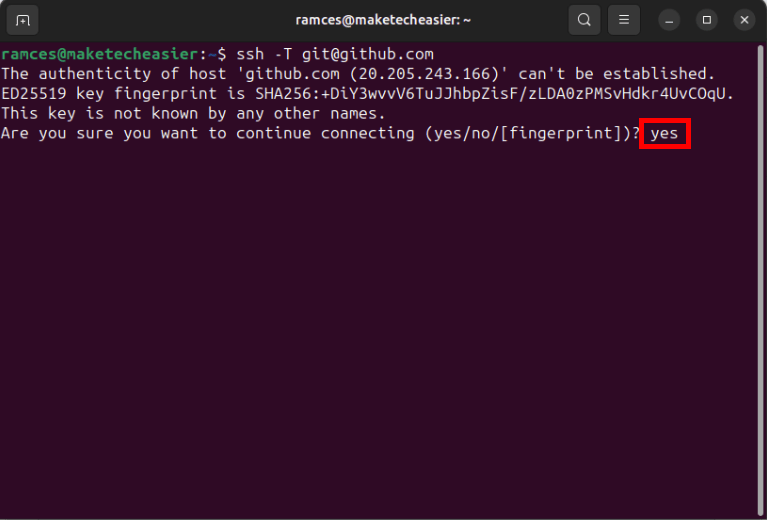
Open a new terminal session and run the following command:
ssh -T git@github.com
Type “yes”, then press Enter.
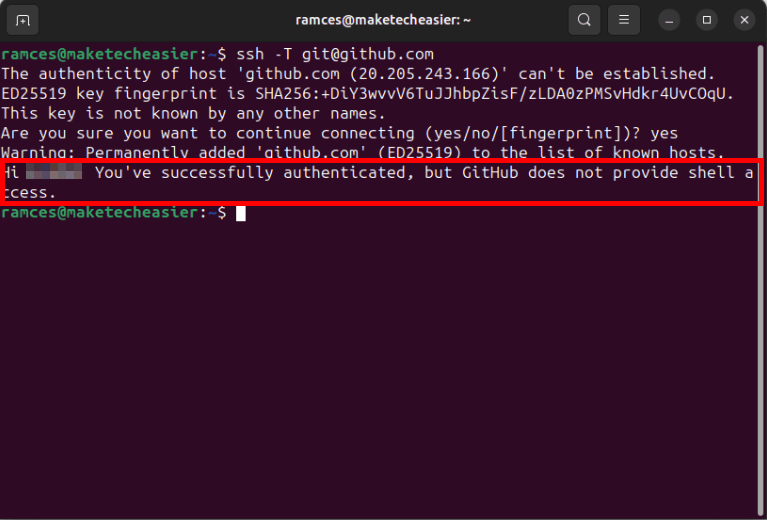
Doing that will start a new SSH session to one of Github’s receiving servers. If your key is working properly, this will print a short message acknowledging your SSH connection.
Managing SSH Keys
While a single SSH key is enough for most users, there are instances where you need to synchronize a Git repository that is hosted across multiple machines. To do this, you need to import machine-specific SSH keys.
Open a new terminal session on the computer that you want to link to Github.
Ensure that the OpenSSH daemon is both installed and running in the system:
sudo apt install ssh eval `ssh-agent -s`
Run the following command to create a distinct SSH key for your new machine:
ssh-keygen -t ed25519 -f ~/.ssh/id-ed25519-pc2 -C "ramces@email.invalid"
Type a secure passphrase for your new SSH key, then press Enter.
Add your new alternative key to your SSH agent:
ssh-add ~/.ssh/id-ed25519-pc2
Print the contents of your SSH public key, then copy it to your system’s clipboard:
cat ~/.ssh/id-ed-25519-pc2
Go back to your Github account’s “SSH and GPG Keys” page.
Click the “New SSH Key” button again.
Provide a unique label for your new key, then paste the contents of your clipboard under the “Key” textbox.
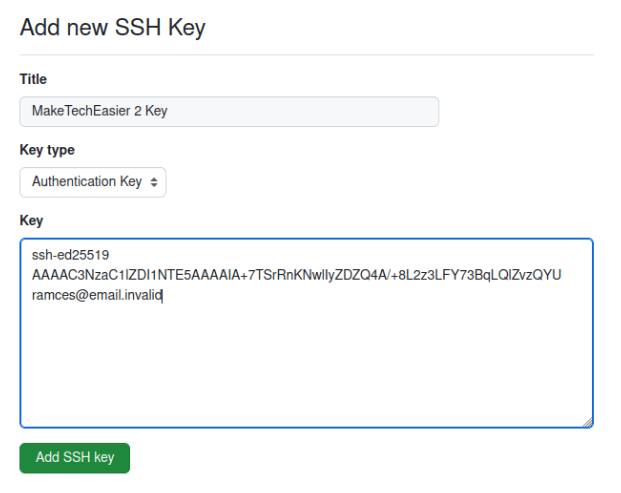
Click “Add SSH Key” to apply your new settings.
Test whether your new machine uses your secure key to connect to Github by logging in through SSH:
ssh -T git@github.com
Modifying Existing SSH Keys
Aside from sending newly generated keys to Github, you can also modify existing SSH keys that you already have inside your machine. This can be useful if you are already using SSH keys as a password-less login in Linux.
To modify an existing key, navigate to your machine’s “.ssh” directory:
cd ~/.ssh
Run ssh-keygen with the -p, -o and -f flags along with your SSH key. This will allow you to change the password on an existing private key:
ssh-keygen -p -o -f ./id-ed25519
Note: You can also use these flags to convert a regular SSH key to a password-less one.
You can also change the embedded email address inside your public key by using the -c flag:
ssh-keygen -c -C "ramces@new-email.invalid" -f ./id-ed25519
Reload your SSH agent with your newly updated key:
ssh-add ~/.ssh/id-ed25519
Replace the corresponding SSH public key from your Github profile.
Removing SSH Keys from Github
Open a new terminal session, then start the SSH agent daemon:
eval `ssh-agent -s`
Run the following command to delete the SSH private key inside your machine:
ssh-add -d ~/.ssh/id-ed25519
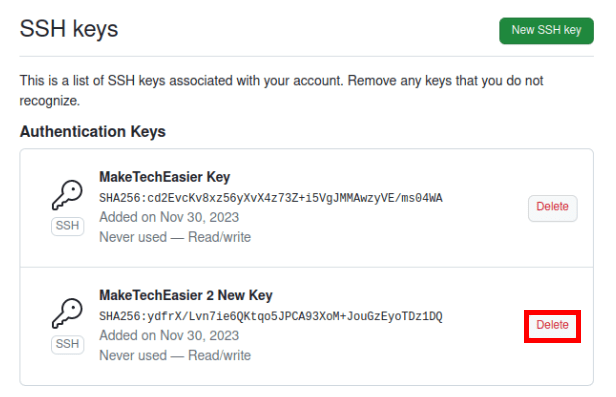
Go back to your Github account’s “SSH and GPG Keys” category.
Scroll through the list of SSH keys on this page, then click “Delete” on the one that you want to remove.
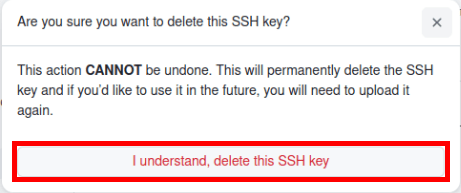
Click “I understand, delete this SSH key.”
Ensure that your old SSH key is now defunct by starting an SSH session to one of Github’s servers:
ssh -T ssh@github.com
Linking an SSH key to secure your Github account is just the first step in understanding how public-key cryptography and encryption work. Learn more about data-at-rest encryption by creating an encrypted cloud backup using Rclone.
Meanwhile, you can also learn more about automatic repository management by using Git hooks.
Image credit: Roman Synkevych via Unsplash. All alterations and screenshots by Ramces Red.
Our latest tutorials delivered straight to your inbox